Enterprise Network Security
As large enterprises and even federal governments still continue to experience high-level cyber attacks, your business depends on the web, email and file exchange. That’s why over 90% of cyber attacks use those communication channels to infiltrate your organization and gain access to your valuable data or cause damage. At Datazone Systems, we’ve helped businesses and organizations from every sector implement successful security policies by empowering them with granular control and visibility while designing a multi-pronged approach to keep their networks safe and secure.
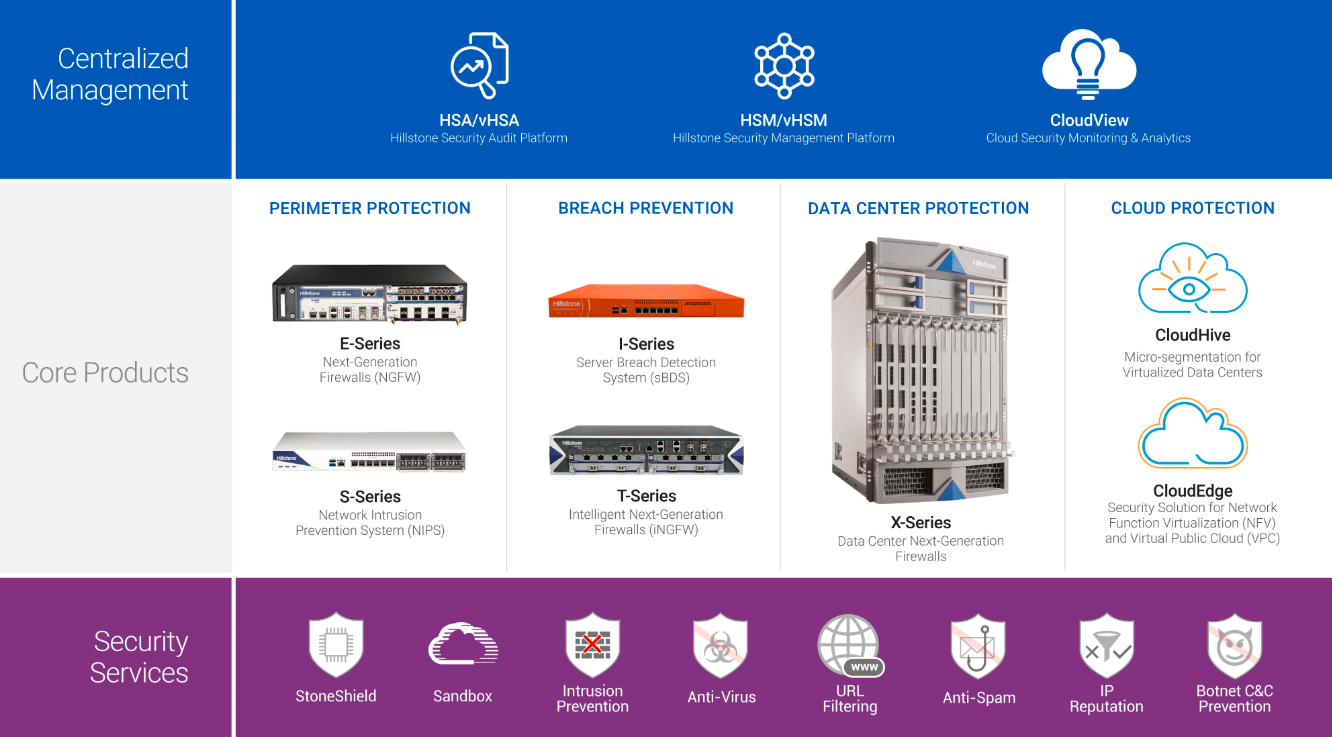
Benefits of enterprise network security:
- Scan data both at rest (file shares) and in motion (email and web traffic) to quickly identify and validate threats.
- Correlate activity across remote and local networks and devices to identify known and unknown (zero-day, blended and targeted) attacks.
- Improve response times and efficiency by prioritizing validated threats with detailed threat intelligence.
- Detect attacks in real time to stop them from spreading through your systems.
- Leverage industry-leading threat intelligence from global deployments and incident response engagements to understand why, how and where threat actors are targeting your organization.
- Eliminate false positives to save time and resources and attend to critical alerts.
- Prioritize real threats with rich contextual insights to better manage your risks.
- Leverage an integrated platform with technology, intelligence and expertise to stop advanced attacks.
- Consolidate reporting, administration and data sharing of threat prevention platforms.